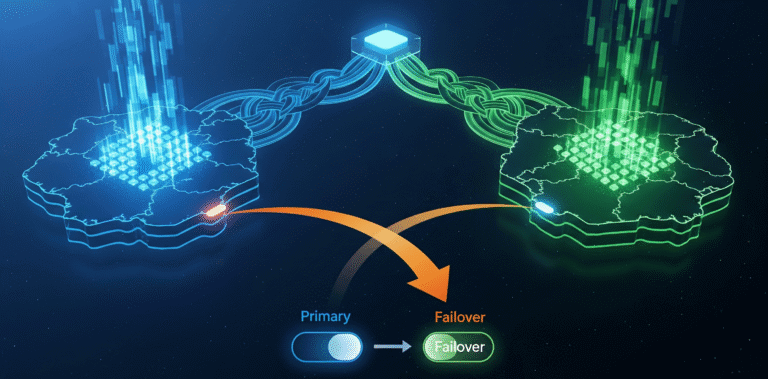
Escaping us-east-1: A Practical Guide to Building Multi-Region Failover with Terraform
The 3 AM pager alert. Slack channels exploding. A single, dreaded message cascades through the organization: “We’re seeing issues with us-east-1.” It’s the outage that every seasoned engineer knows is not a matter of if, but when. I’ve walked into companies where their entire multi-million dollar operation was pinned to a single AWS availability zone,…